NSS小记1
NSS小记1
记几道NSSCTF上面的题目
new_fast
题目保护情况(保护全开)
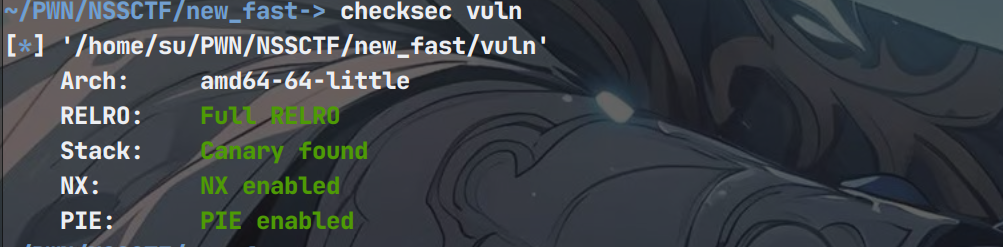
64位ida逆向看看
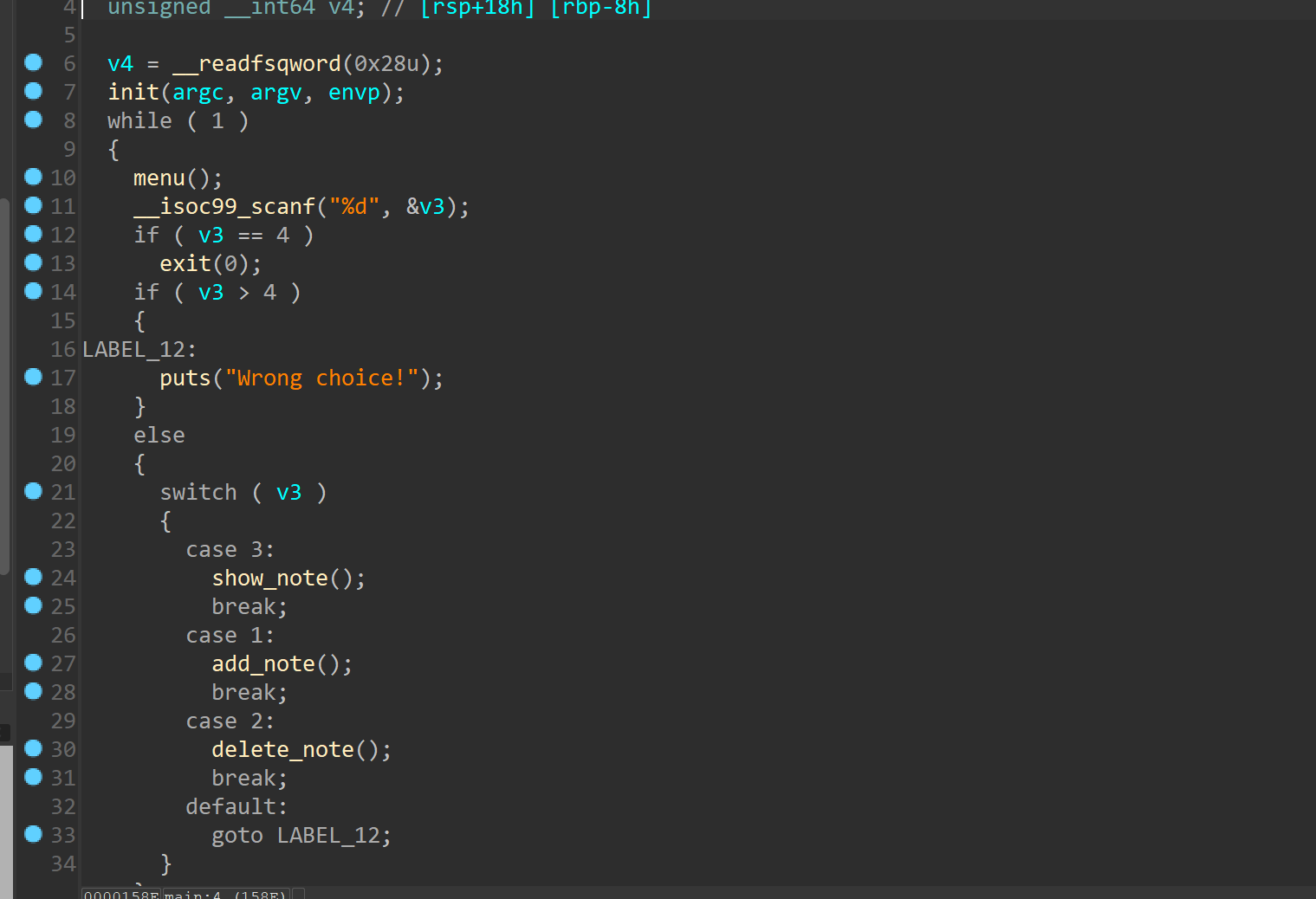
3个功能,add,show,和delete
我们重点看看delete
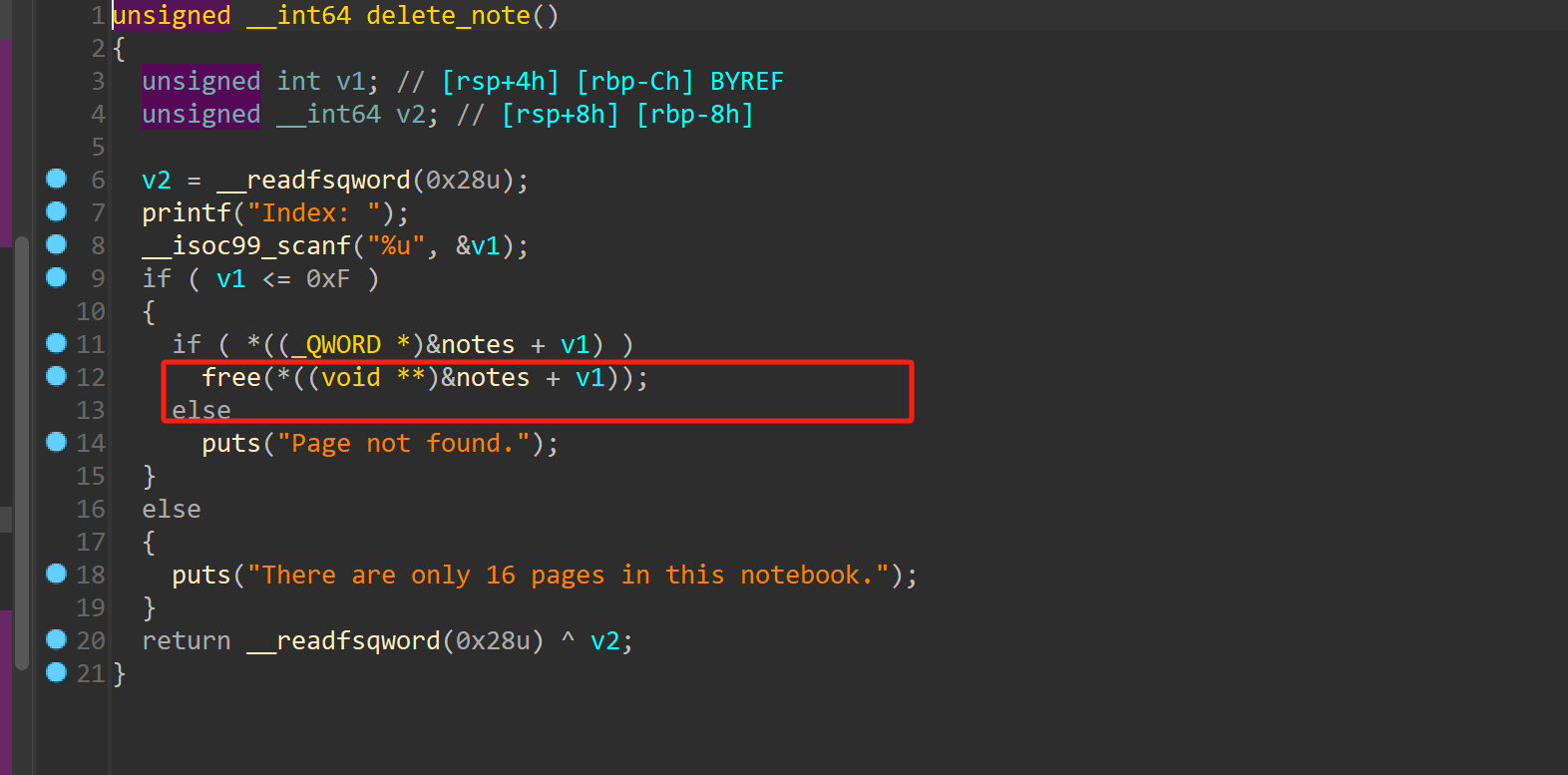
存在UAF漏洞
add函数最多不能申请堆块大小超过0xff,数量是0x13,puts有00截断
分析
程序libc是2.31的存在tcachebin机制,但是因为存在UAF,所以可以delete7个堆块把tcachebin填满,然后剩下堆块进入unsottbin 泄露libc,再次申请堆块进入fastbin,进行doublefree fastbin attack,但是后来发现,当tcachebin链表为空时,fastbin中有2个及以上的堆块的时候,会进入到tcachebin 堆块,这样就可以打tcachebin 劫持free_hook了
exp
1 | |
duck
题目保护情况(保护全开)
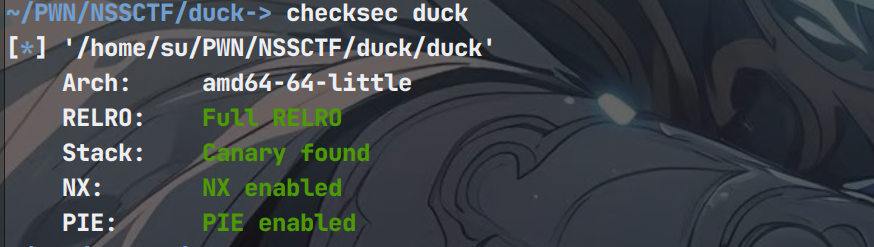
64位ida逆向
功能很全,有add,del,show,edit
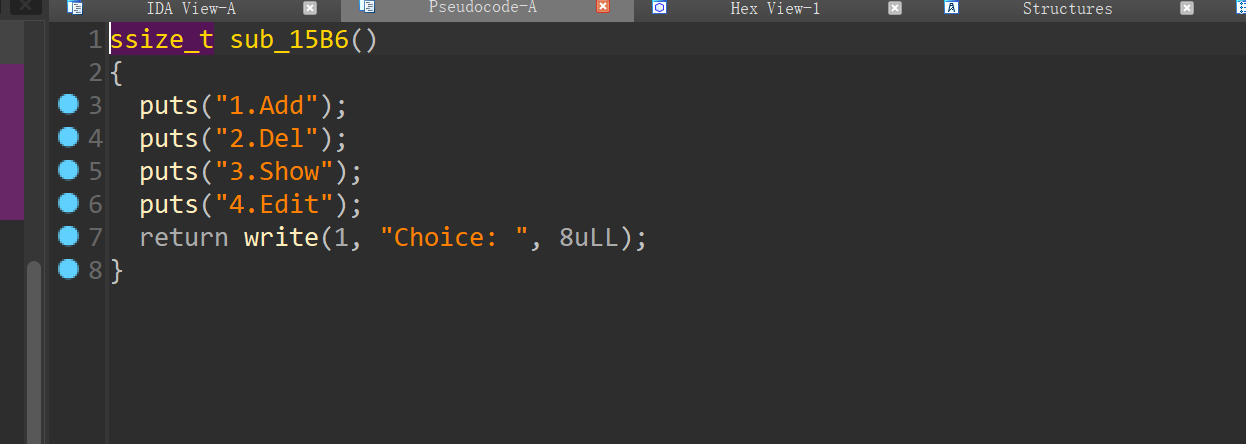
del同样存在UAF
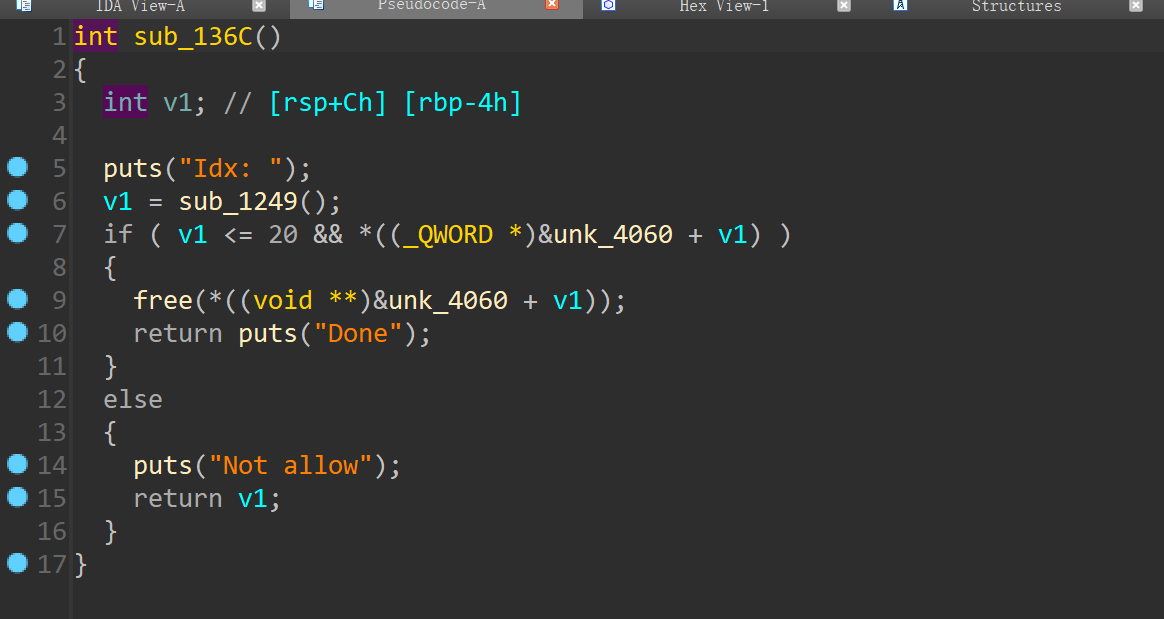
add申请堆块固定
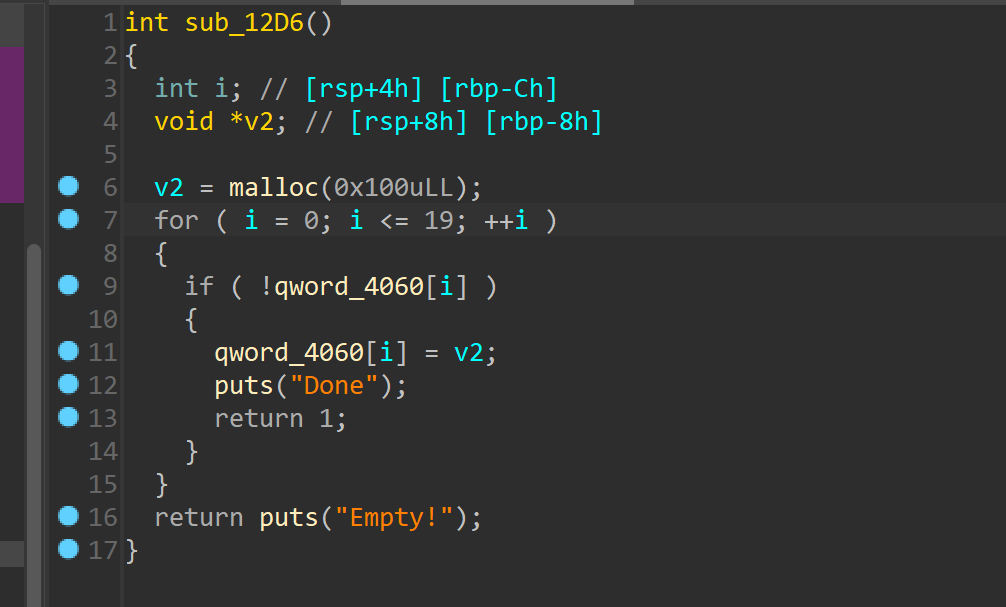
show,调用puts存在截断
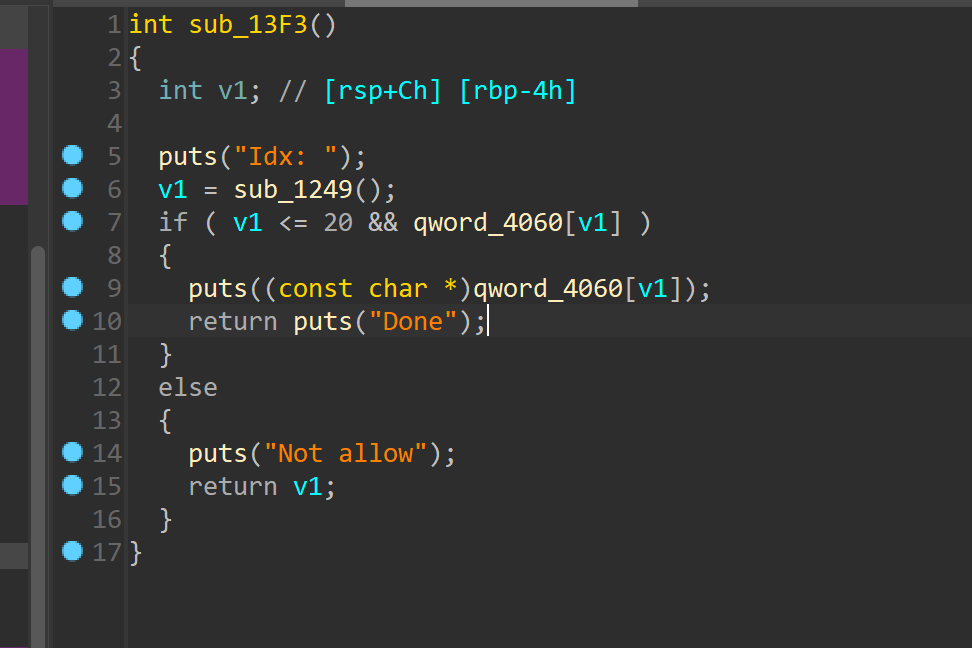
edit函数
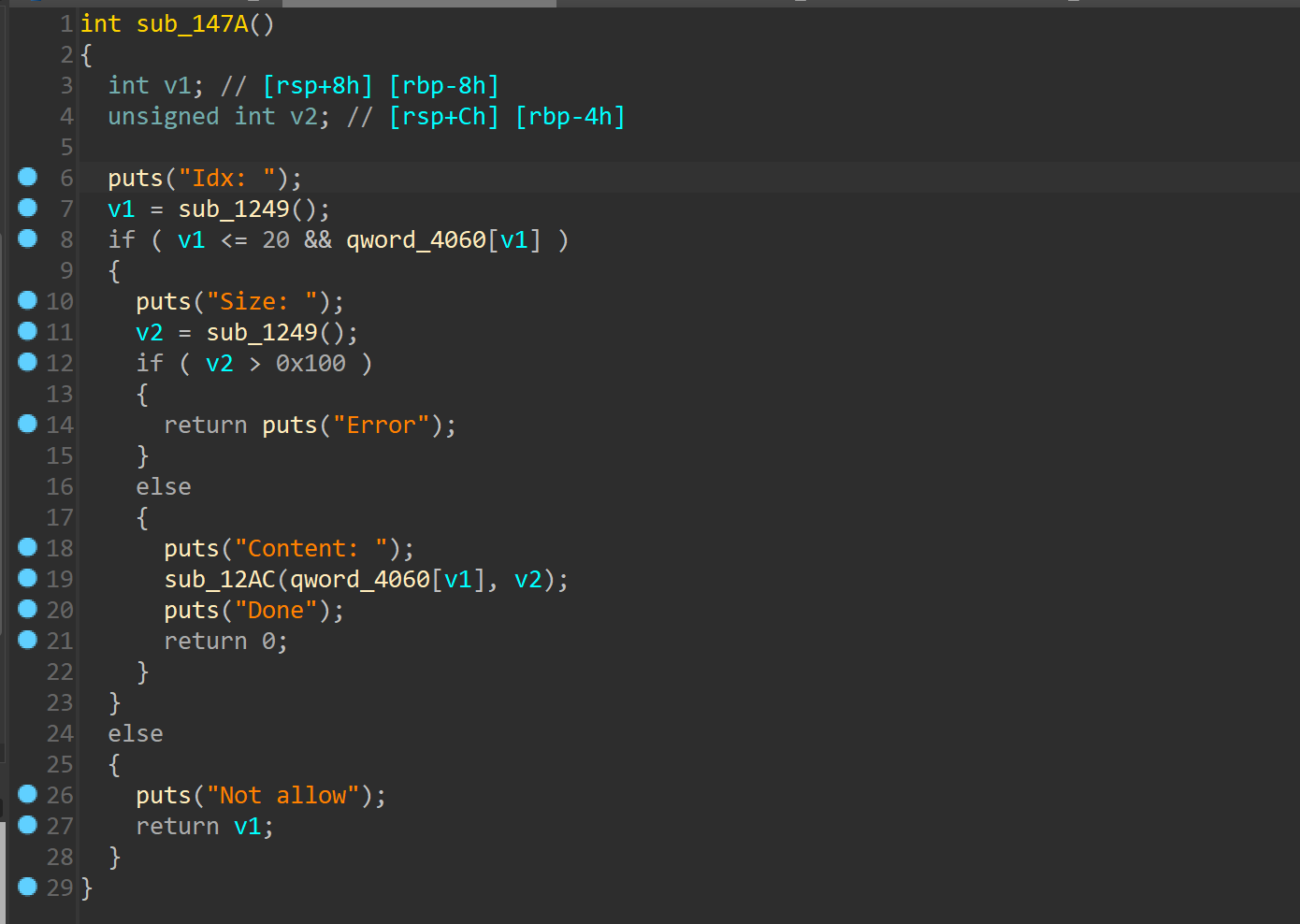
分析
本地libc版本是2.34版本,自2.31版本之后引用了fd,bk指针加密,加密方式 fd ^ heap >> 12
泄露libc地址的话还是可以通过填满tcachebin的方式获取
因为2.34libc不存在malloc_hook 和free_hook等这些钩子,但是程序调用了puts,puts最后会调用__SI_IO_new_file_xsputn_12
然后 SI_IO_new_file_xsputn_12调用 __SI_IO_new_file_overflow_8,因此我们劫持 _IO_file_jumps 来劫持 _IO_new_file_overflow最终拿到shell
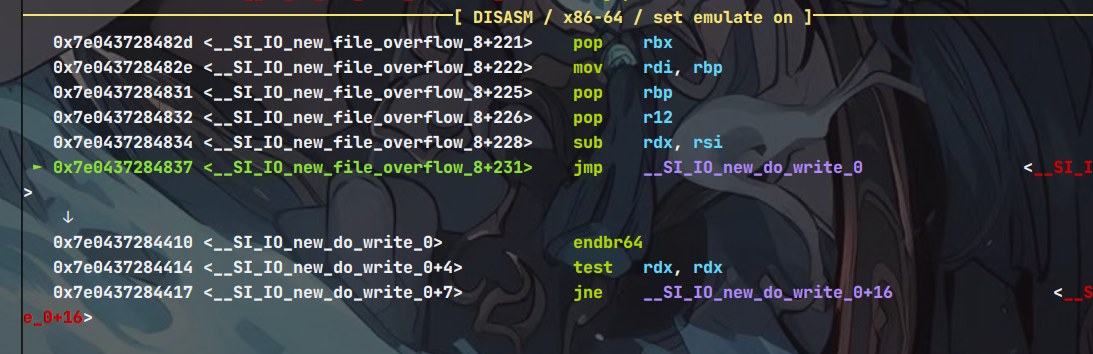
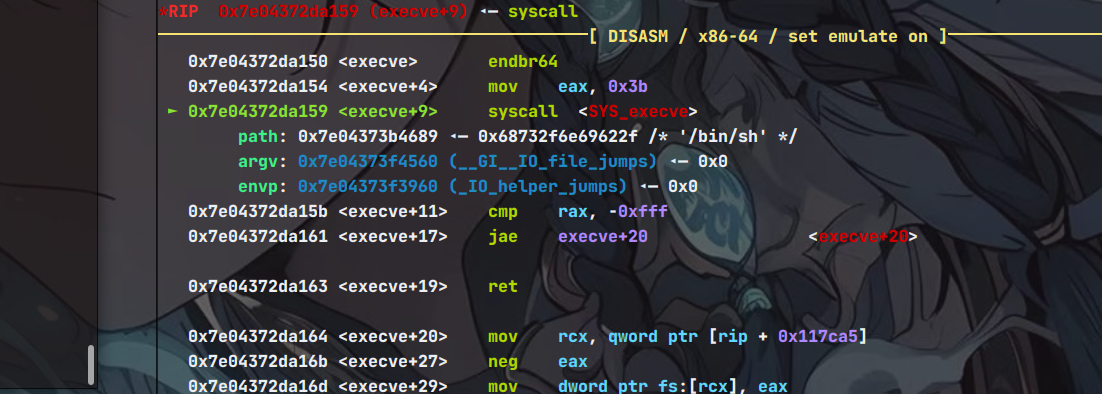
exp
1 | |
bigduck
程序保护情况(保护全开)
程序开了沙箱考虑orw
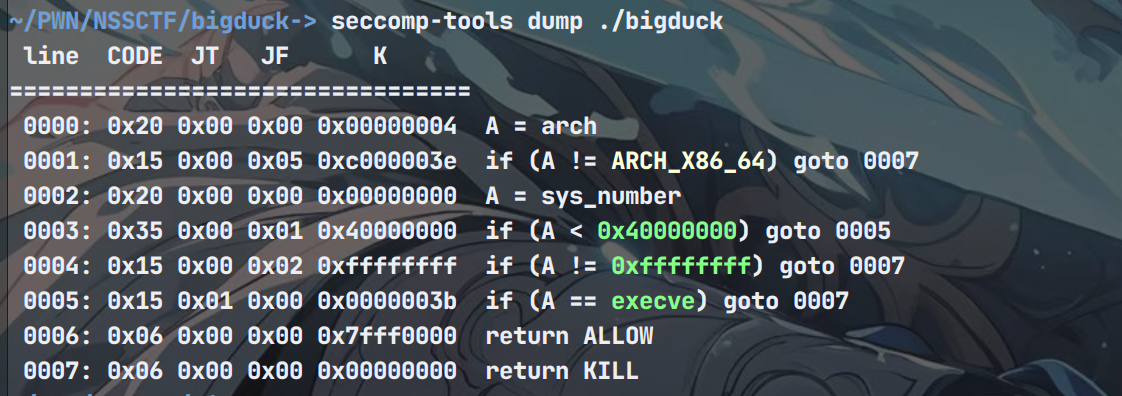
64位ida逆向
跟duck很像
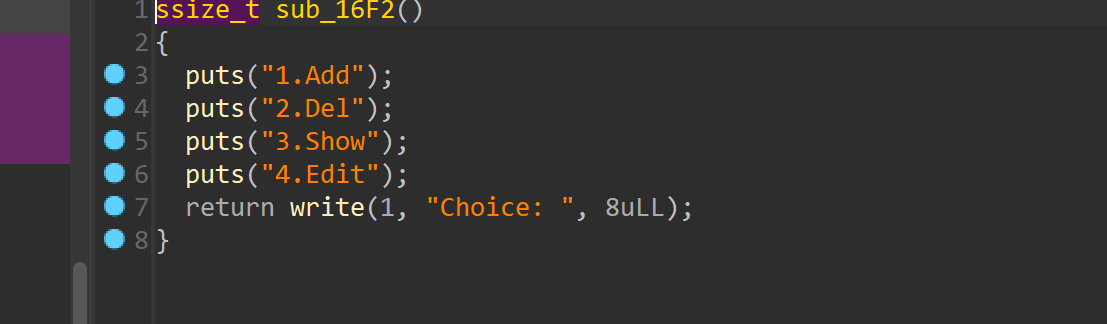
那么函数就不再分析了,唯一的区别这个libc是2.33的存在钩子什么的,但是开了沙箱不好劫持
分析
我这题的做法是通过UAF,来double free 劫持 tcache_ptheread_struct结构体,进而控制tcachebin,这样就可以劫持到栈上,劫持返回地址来打ROP,但是要注意,2.33的 tcache_ptheread_struct结构和2.27不一样,2.33大小是0x290,每个链表长度占2个字节,
思路就是先泄露heap地址,劫持 tcache_ptheread_struct来泄露libc地址,然后得到environ地址,进而打印出栈上的地址,然后还是通过劫持 tcache_ptheread_struct结构体来申请堆块到栈上,读取flag
exp
1 | |